Deploy Secure ecommerce Workloads on Amazon Web Services – AWS
Ever since the COVID-19 virus came into our lives things have changed dramatically, followed by recent lockdown throughout the country which have created different types of problems for normal people, business owners and other vendors. Not only this but existing online ecommerce businesses like Amazon have also been hit badly due to logistical issues and nationwide restrictions.
Lockdown and other restrictions have forced many business owners to think and explore online business solutions for their customers. There has been an increasing number of inquiries to explore and start online selling stores to reach the customers directly. As an example we have seen many small vendors like General stores, Food products, Vegetables vendors have started looking to provide online services for their customers, in fact some of them have even started.
I agree it’s a good step to offer online services to cater your customers’ requirements. However, one major doubt the vendors have in mind while discussing and planning for their deployments is that will the data be secured? Should we host our platform on shared hosting? VPS or dedicated server? Or AWS is a good choice.
Our experience and being a managed service provider with AWS is whether its Magneto or any other eCommerce platform, Application security at AWS is the highest priority. AWS is a platform that allows you to formalize the design of security controls in the platform itself.
Hence understanding the shared responsibility model of AWS is very important to understand the security principles and foundation of AWS. Let’s see below and learn some security about AWS.
Share Security Responsibility with AWS
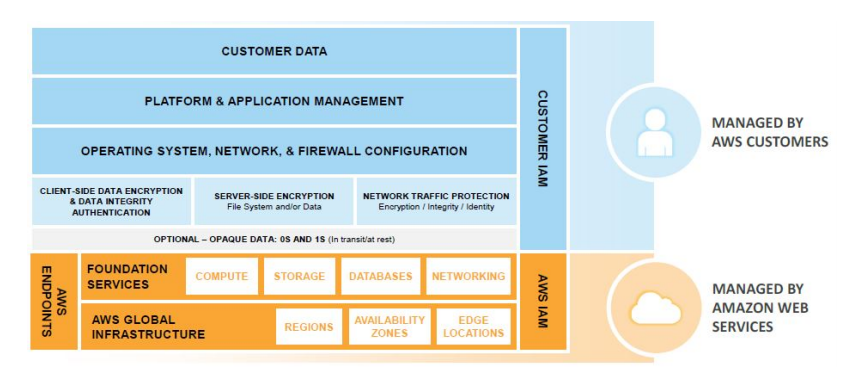
AWS operates under a shared security responsibility model therefore AWS is responsible for the security of the underlying cloud infrastructure and you are responsible for securing the workloads ( instances or VMs ) that you deploy in AWS.
This explains in simple words that AWS is responsible for the underlying infrastructure security like Physical security of hardware, Network infrastructure (for example to prevent DDOS attacks) & Virtualization infrastructure. The customer is responsible for the security of his assets like host operating system like Centos, Ubuntu or Debain, PHP Applications, Mysql Databases and the data which is hosted on the server itself. The following diagram gives a clear understanding about the shared security responsibility model.
As we are going to discuss about customer’s asset security, following points will help you to understand how to secure your application.
Secure Your Operating Systems and Applications
- Disable root API access keys and secret key
- Restrict access to instances from limited IP ranges using Security Groups- This is very important and allows to secure access for our applications. A security group is a set of firewall rules that control the traffic for your instance
- Apply updates and patches for your operating system, harden the host operating system.
- Remember to delete keys from the authorized keys file on your instances when someone leaves your organization or no longer requires access
- Install latest software’s and make sure your application is compatible with the latest versions. Do not use EOF software versions for example. PHP 5.6
- Change default SSH port and restrict access with limited IPs from security group.
- Use bastion hosts to enforce control and visibility
Secure Your Infrastructure
On AWS, you can secure network segments using the following access control methods:
- Using Amazon VPC (Virtual Private Cloud ) to define an isolated network for each workload or organizational entity.
- Using security groups to manage access to instances that have similar functions and security requirements; security groups are stateful firewalls that enable firewall rules in both directions for every allowed and established TCP session or UDP communications channel.
- Using Network Access Control Lists (NACLs) that allow stateless management of IP traffic. NACLs are agnostic of TCP and UDP sessions, but they allow granular control over IP protocols (for example GRE, IPSec ESP, ICMP), as well as control on a per-source/destination IP address and port for TCP and UDP. NACLs work in conjunction with security groups, and can allow or deny traffic even before it reaches the security group.
- Using host-based firewalls to control access to each instance.
- Creating a threat protection layer in traffic flow and enforcing all traffic to traverse the zone.
- Applying access control at other layers (e.g. applications and services).
Secure Your Data
To secure your data and protecting data at rest and in transit on the AWS platform you might want to use Amazon S3, Amazon EBS, Amazon RDS, or other services from AWS.
Amazon S3 (Simple Storage Service) providers a number of security features to protect your data at rest. By default, data at rest is secured and encrypted.
Manage Security Monitoring, Alerting & Audit.
The shared responsibility model requires you to monitor and manage your environment at the operating system and higher layers. Use Cloudwatch or any other monitoring tool like Datadog or Nagios which can give you better insights details of your infrastructure. Datadog is an excellent tool to detect and investigate security threats in real time.
Built-in Security
Security at AWS is the highest priority, which means that you benefit from data centers and network architecture that are built to meet the requirements of the most security-sensitive organizations.
For more references please visit AWS Security Best Practices