Cloud and Host Server Security: Tips and Tricks to ensure safety
The number of cloud users is increasing year after year. For a safe and secure storage, cloud server has become an eminent option to keep the information intact and safe. Emails are rarely chosen these days to send a bunch of photos or usages of USB or flash drives has also become rare to carry documents.
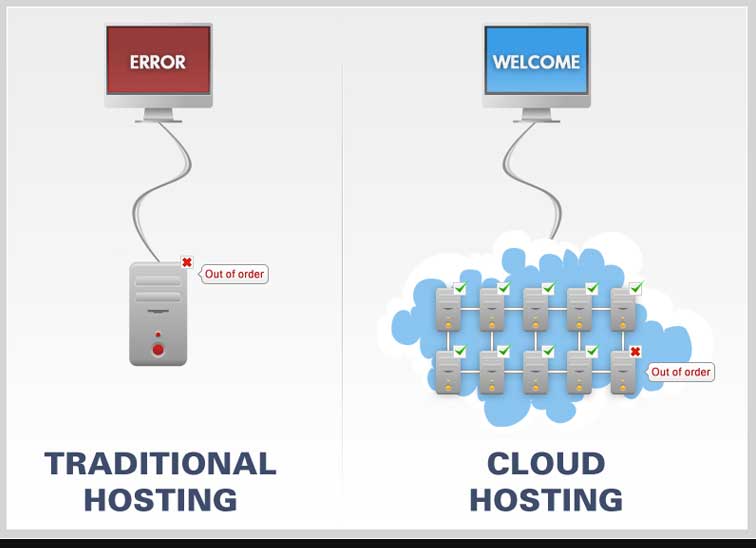 The question of security of servers arises in the case of both whether the servers are physically hosted or virtually kept. Few tips and tricks we are mentioning below to ease off this complexity of securing the data with the cloud and host servers:
The question of security of servers arises in the case of both whether the servers are physically hosted or virtually kept. Few tips and tricks we are mentioning below to ease off this complexity of securing the data with the cloud and host servers:
1. Usage of 2FA Factor and formation of strong passwords is strictly recommended
There should be a complexity maintained in the formation of passwords. The inclusion of special characters, a numeric value or a combination of case letters and at stretch length of a minimum of eight characters should be mandatory to lay the foundation for hassle-free logins. Passwords should be changed regularly.2F authentication can also be implemented to guarantee the safety and security of the websites. Never a password should be repeated so as to avoid the hacking of passwords and respectively the websites.
2. Authorize the usage of encrypted key
The encryption of the information which is stored in the cloud can be executed in two different ways. Confined encryption can be recommended by varied service providers. In this particular case, the encrypted format of the data is saved in the cloud without making any changes. Encrypting a data is not a simple process, rather a tedious task which consumes a good amount of time to transmit and receive data. To organise the transferring of data and the encryption process, there can be a composite usage of hardware and the software.
Encryption is not only done with the data on the cloud, it can also be preceded locally much before executing it on the cloud server. Encryption of the cloud data can be done, also it can be done locally before it is sent on the cloud .this is done in case of many businesses where data is required to possess a maintenance of high level of security and confidentiality,
3. Back up has got no substitute
Even if the data is fully encrypted and stored on the cloud server, that does not reduce the necessity of backing up the data explicitely.There can be times when occurs a permanent system failure, a duplicate or replica of data’s copy should be maintained as well. Especially to store a confidential data of the large corporates or big business entities so as not to land up with the discontinuation of their service
4. Proper inclusion of policies to be established
Security of the information or the data is also dependent on the platform of connections used for internet services. There are times when Wi-Fi connections are not secured. Since the features of cloud server can be accessed from any remote location with the help of single or 2Fauthentication process one can establish an internet connection to approach the same. There should be protocols defined to access the same so as to avoid any unsecured logins to the system.
 5. Whether there are dedicated servers or virtually present servers, all communications should be well secured
5. Whether there are dedicated servers or virtually present servers, all communications should be well secured
Rules and regulations commonly termed as protocols should be in lieu of the service provider since the access to the secured cloud server moves from that of a simple communication by the end user to large business corporates. At times an unencrypted communication also falls in place in case if the security of the encrypted data fails, in that case, the access to the information should also fail. If the information is not secured. It implies again that ‘IT IS JUST NOT SECURED’!
6. Smartphone access to the cloud information should be controlled too
Nowadays there are many apps available in the stores to ensure the access to information to the mobile users. There should be a proper control policy made so as to make sure that there cannot be any compromise made as far as the security of the data is concerned. The applications which run on these remote devices should be well scrutinized before they land up into troublesome issues.
7. it’s your right since it’s absolutely your data!
An exchange of data or the data itself, both are never stagnant. There is hell of information or data which is just not allowed to be exchanged or stored or shared on any platform. The information can be in regards to confidential policies, employee’s complete profile with salary structures and increment details, the deductions which are to be kept safely, the comparison charts and scale etc. these are the information which we just cannot compromise with, we should have keen knowledge of what the information is about and where on cloud it is stored so that once it is of no use to the business entity it can be archived or deleted permanently.
8. Be clarified of the contractual terms
Do ensure whatever is promised or being approached to you with is observed sequentially or not. There should be no compromises and failures in regards to the data security.
9. Patient fully keep testing until you are satisfied
There are various assessment tools available to ensure whether the data is secured on the cloud server or not. One should keep testing and scanning the security with different sources and tools so as to develop a proper assurance of the safety feature.
10. Dare not to compromise with the safety issues
Let the security be your responsibility, a stream of helpful hands will always be at work. They can range from dedicated or virtually hosted cloud servers, but it’s your duty to land up creating a foolproof secured plan and its safe execution. Let your entity to never be a part of new leakages.





