PCI Compliance Checklist – How to resolve Vulnerabilities.
What is actually PCI Complaince and why it is required?
The PCI (Payment Card Industry) is a data security standard that must be followed by all the financial institutions, credit card companies, Payment gateway and merchants those are processing the online card payments. The server, computer or any other IP equipment’s processing these data by MasterCard, American Express, Discover, Visa, and JCB International must compliance with these Data Security Standards. PCI scan is very essentials and should meet these Data Security Standards to help you protect from any types of frauds, security vulnerabilities and identifying thefts. The PCI scan is conducted by Approved Scanning Vendor (ASV) like McAfee, Hacker guardian, Trust guard etc. Importantly, the PCI scan must be conducted quarterly (at least every 90 days) to stay up to date with the latest security vulnerabilities as well as security holes in order to protect your company from any expensive costly breaches. Reassuring the visitors that the website is safe and secure to accept card payments.
We will try to understand the basics of PCI scan given below.
Some of the server side parameters (specific software packages) that you should consider for PCI those are known to contain vulnerabilities.
Lets look in some more detail about how we can resolve the vulnerabilities reported by the scan report. I will recommended to get PCI scan conducted with Approved Scanning Vendor.
https://www.pcisecuritystandards.org/assessors_and_solutions/approved_scanning_vendors
You can scroll down a bit and see ( Find an Approved Scanning Vendor Company )
1.Sign in with ASV.
Sign up with either of the ASV companies which you think is good and who will conduct external and internal scanning based on PCI DSS.
2.Initiate a PCI scan.
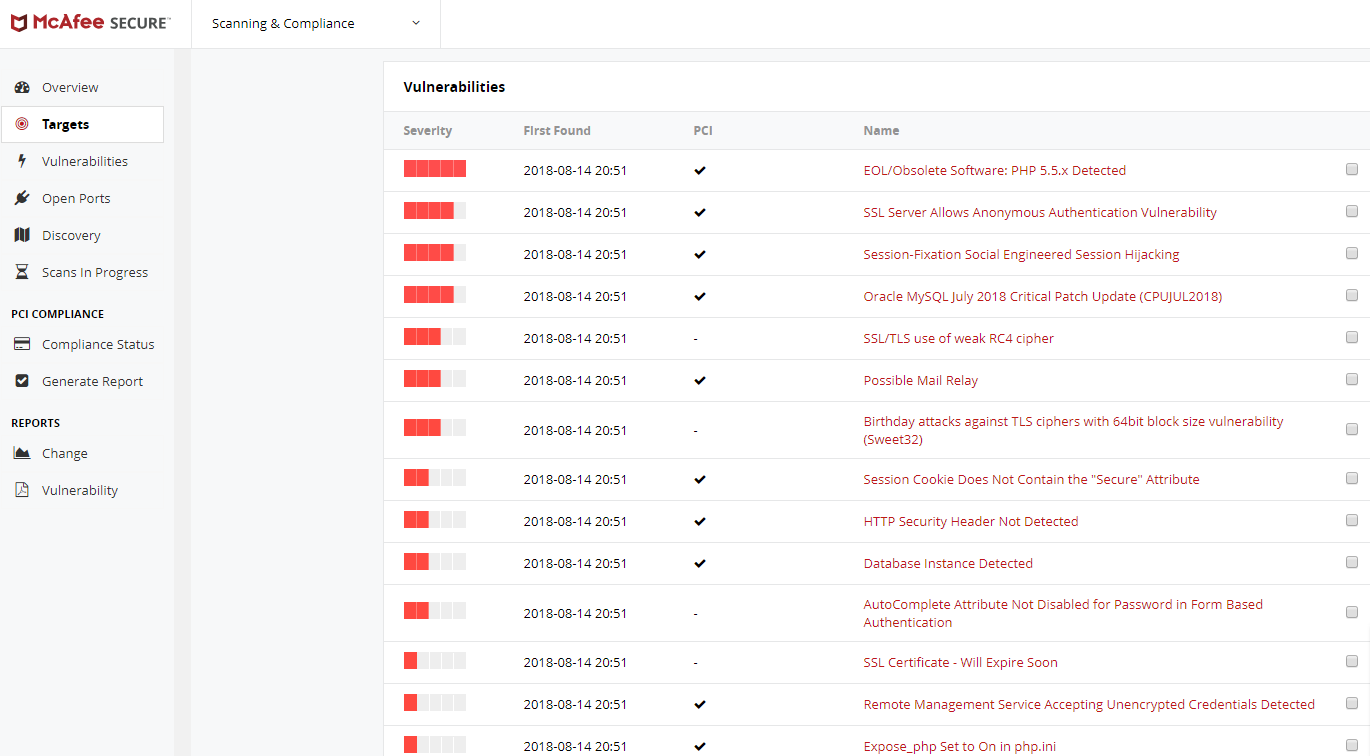
The scan will take a couple of hours to scan the targeted domain. Upon completion, it will result in the complete summary report of the vulnerabilities, Disclosures and the open ports. Each and every identified vulnerability will be listed one below the another along with an explanation on the action to be taken along with the server-side patches those needs to be applied to fix the issue.
For example, the scan report is from McAfee.
| Severity | Scan Date | Vulnerabilities | Disclosures | Open Ports |
| 2018-08-14 20:51 | 14 | 27 | 15 |
Following are the actual vulnerabilities reported which needs to be resolved one by one directly from the server.
Vulnerabilities #1
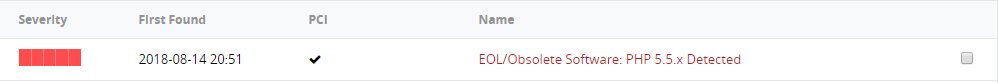 How to Fix: It has been noticed that the website was on PHP 5.5 which is now deprecated and EOL. Try changing the website version to PHP 5.6 or higher.
How to Fix: It has been noticed that the website was on PHP 5.5 which is now deprecated and EOL. Try changing the website version to PHP 5.6 or higher.
Vulnerabilities #2
![]()
How To Fix: For Apache/apache_ssl include the following line in the configuration file:
SSLRequireCipher ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM
Vulnerabilities #3
![]()
How To Fix: Enabled “session.use_only_cookies”, this allows PHP session IDs to be set only via HTTP cookies.
Vulnerabilities #4
![]()
How To Fix: False alert reported. Oracle software not installed on our server.
Vulnerabilities #5
![]()
How To Fix: Update SSLProtocol -ALL +SSLv3 +TLSv1 in the Apache configuration.
Vulnerabilities #6
![]()
How To Fix: Limit number of emails per hour on the server.
Vulnerabilities #7
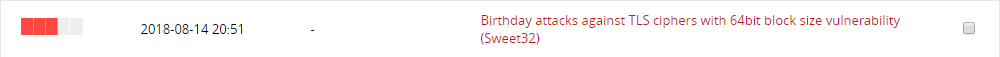
How To Fix: Disable DES, 3DES, IDEA or RC2 ciphers , the Ciphers updated above in the Apache configuration should take care of this too.
Vulnerabilities #8
![]()
How To Fix: Apply the “secure” attribute to session cookies to ensure that they are sent via HTTPS only.
Update the following code in .htaccess file.
Header always edit Set-Cookie (.*) “$1; HTTPOnly”
Header always edit Set-Cookie (.*) “$1; Secure”
Vulnerabilities #9
![]()
How To Fix: Update following codes in .htaccess file as per the vulnerabilities shown.
- Code for Apache
# X-Frame-Options
Header always append X-Frame-Options SAMEORIGIN
- Code for Nginx
# X-Frame-Options
add_header X-Frame-Options SAMEORIGIN;
- Code for HAproxy
# X-Frame-Options
rspadd X-Frame-Options:\ SAMEORIGIN
- Code for IIS Web Server.
# X-Frame-Options in web.config file:
<HTTPPROTOCOL><CUSTOMHEADERS><ADD NAME=”X-Frame-Options” VALUE=”SAMEORIGIN”></ADD></CUSTOMHEADERS></HTTPPROTOCOL>
- Code for Apache
#X-XSS-Protection
Header always set X-XSS-Protection “1; mode=block”
- Code for Apache
#X-Content-Type-Options
Header always set X-Content-Type-Options: nosniff
Vulnerabilities #10
![]()
How To Fix: Open MySQL port for only specific remote IP’s you want to provide access to or disable 3306 port completely on the server. Contact us if you would like us to do it.
Vulnerabilities #11
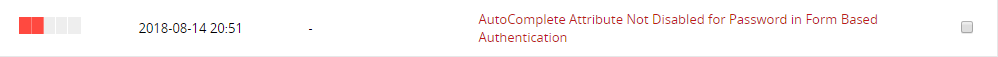
How To Fix: You will need to contact the vendor/ developer of the website to have the Auto complete attribute disabled for the password field in all forms.
Vulnerabilities #12
![]()
How To Fix: Purchase a Valid SSL certificate and install it on your domain.
Vulnerabilities #13
![]()
How To Fix: Disable FTP port and use SFTP instead. Again contact us if you would like us to do it.
Vulnerabilities #14
![]()
How To Fix: Update php.ini file and update the parameter expose_php = Off.
3. Finally Addressing the failed scan.
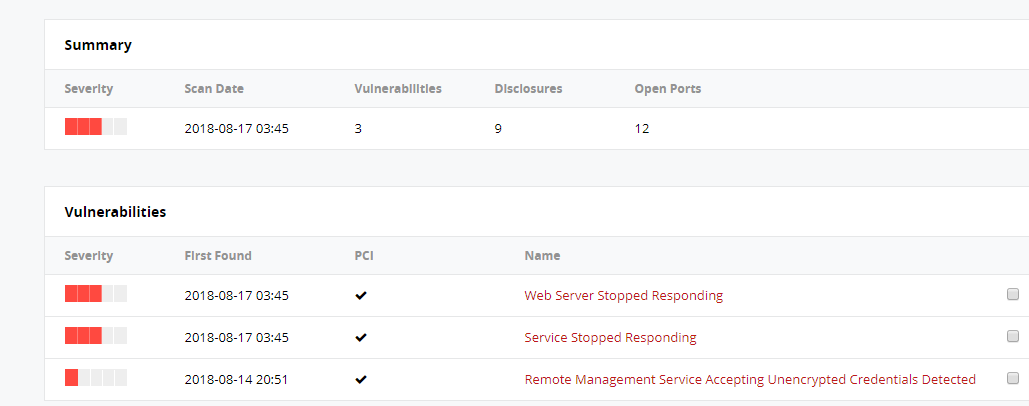
The server administrator must go through each and every vulnerability that has been listed in the scan report and address them individually. You must consider fixing the reported vulnerabilities on the server side.
Re-scan the domain once you have applied the fix and patches. The second report will provide you a complete summary about the vulnerabilities, this will assure you that if you have missed any vulnerability as well the fixes that you have applied for prior reported vulnerabilities are correct or not.
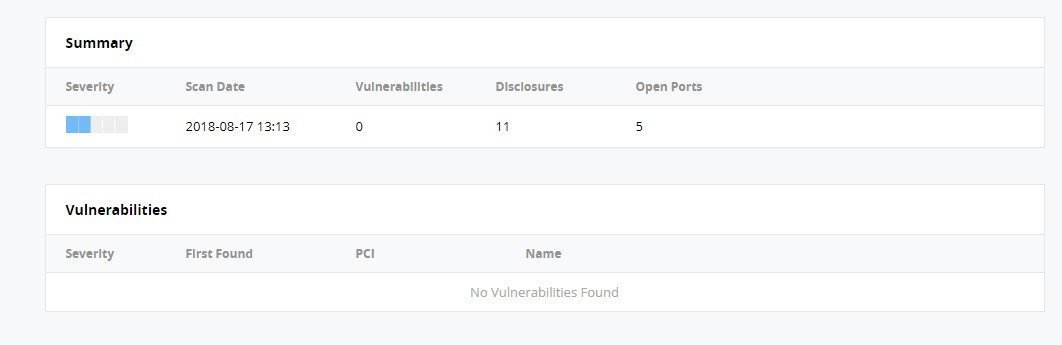
Once the administrator has taken care of the reported vulnerabilities. They can re-run a scan as a final testing. The report should look the below screenshot showing no vulnerabilities found. Looks good !! Isn’t it ? This means your work is done and you can now send this report for an approval.
| Severity | Scan Date | Vulnerabilities | Disclosures | Open Ports |
| 2018-08-17 13:13 | 0 | 11 | 5 |
Screenshot: No vulnerability found final PCI summary report.
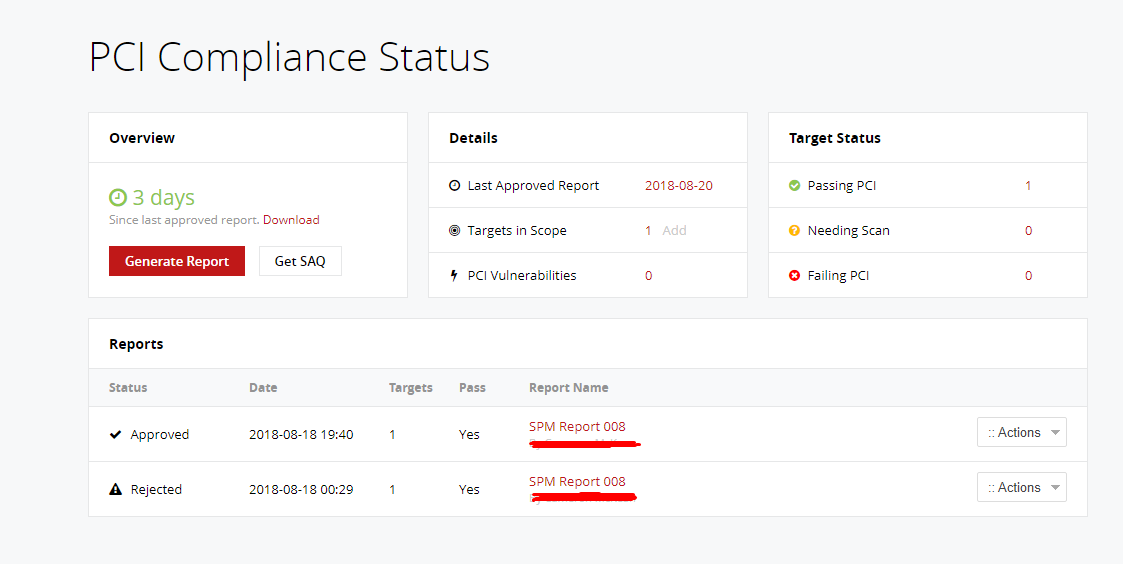
4. Send an approval request.
Check the final report and reassure with ASV and wait for their approval. You can let them know about any false positive alert as well, while reporting. If all goes through perfectly then the PCI compliance status must say Approved.
If you would like to hire our expert security services for resolving the issues related with PCI Compliance Vulnerabilities, You can simply sign-up our PCI-Compliance Plan and submit a ticket. Our experts will assist you to get through this tedious task.